Earlier, I’d written about how to install an SSL certificate in just a couple of clicks using cPanel’s “Let’s Encrypt” plugin. Most hosting providers now offer this functionality, and you can transform your HTTP site into a secure HTTPS site in a few minutes without much hassle.
However, if you’re using Cloudflare, there can be complications. For example, wp-tweaks.com uses Cloudflare’s services to speed things up. For this reason, I suggest you use Cloudflare’s 15-year origin certificates. Before I started using them, my site used Let’s Encrypt, as shown here:
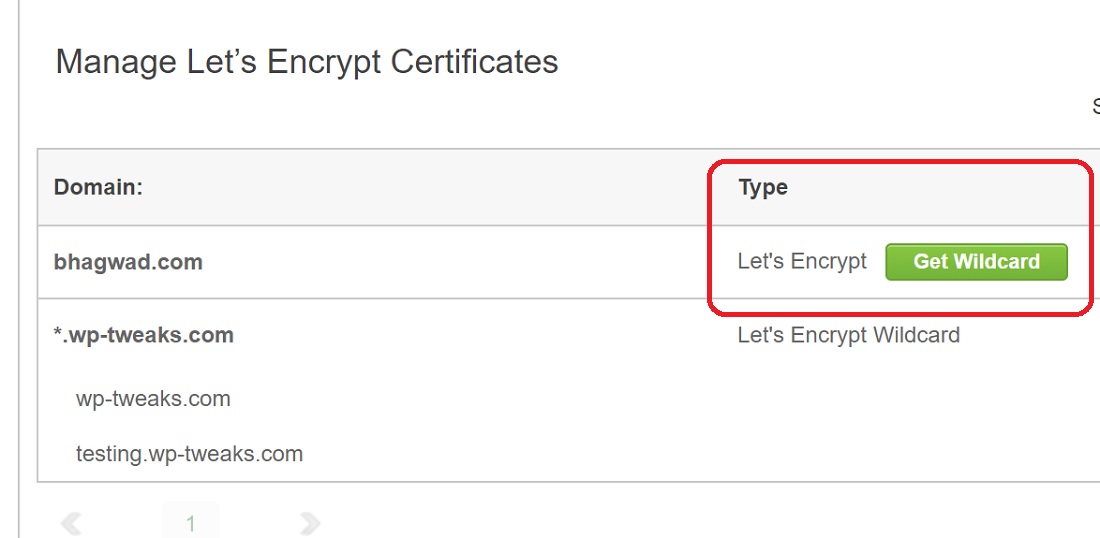
Most web hosts offer Let’s Encrypt for free, so you never need to buy an SSL certificate. You can see in the screenshot that my domain has a “Let’s Encrypt” certificate. However, when I open the site in a regular browser, it shows a different certificate instead:
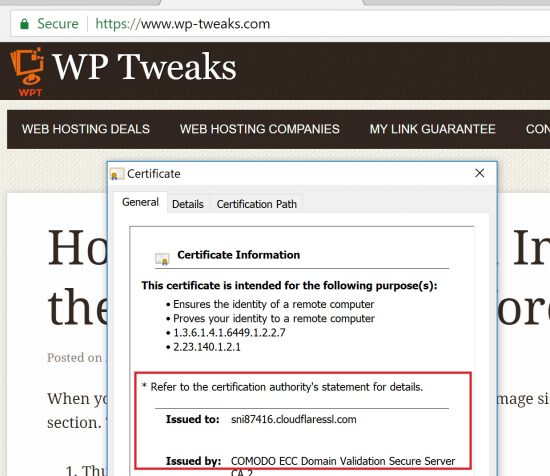
Why Does a Cloudflare Certificate Show instead of Let’s Encrypt?
Many websites have Cloudflare integration. Since Cloudflare increased its fees for Cloudflare cPanel integration, the number of hosts offering one-click integration has decreased. But you can always integrate Cloudflare manually by changing your DNS servers.
Cloudflare caches your content on its servers and then serves it to browsers. So when you access a domain using Cloudflare, you’re not accessing the origin server but Cloudflare’s servers. As a result, you never see the encrypting certificate of the origin server – only that used by Cloudflare. Which is, of course, a Cloudflare SSL certificate!
Does this Mean you Don’t Need an Origin Certificate?
If your certificate is going to be hidden by Cloudflare, the natural question is whether you need an original certificate on your server. After all, there’s no point in setting something up at your end if your content will be served from a different server, right?
While it’s true that you can get away with not setting up an origin server, I wouldn’t recommend it for the following reasons:
No Encryption Between your Server and Cloudflare
The most obvious reason to use SSL on your origin server, even with Cloudflare, is so that the traffic between the origin and the Cloudflare cache is encrypted. If only Cloudflare SSL is enabled, then every time Cloudflare accesses your site, it’s doing so via plain text. This is insecure and doesn’t reap the benefits of end-to-end SSL because you’ve introduced a vulnerability.
A hacker could intercept the traffic between the two points and introduce their content, and Cloudflare will never know. Then your users would be fooled into thinking that they’re getting accurate content from your server because of Cloudflare’s SSL certificate, but in reality, it’s not secure.
Unable to use the Full (strict) Option with CloudFlare
When enabling the “Crypto” option in Cloudflare, you have the choice between the following options:
- Off
- Flexible
- Full
- Full (strict)
The “Full (strict)” option is the most secure, where Cloudflare will validate your origin server SSL certificate with each request. If you don’t have a trusted SSL certificate on your origin server, you’ll have to use a less secure option like “Flexible” or “Full”.
So if you want proper security, you need to get a certificate for your origin server even while using Cloudflare!
Pause Cloudflare Temporarily to See your Site’s Origin Certificate
Suppose you want to verify that your origin Let’s Encrypt certificate is installed correctly. In that case, you can always pause Cloudflare for a short while so that your requests will be served directly instead of via an intermediary. Do this by going to “Overview” in the Cloudflare interface and then choosing “Pause”, as shown here.
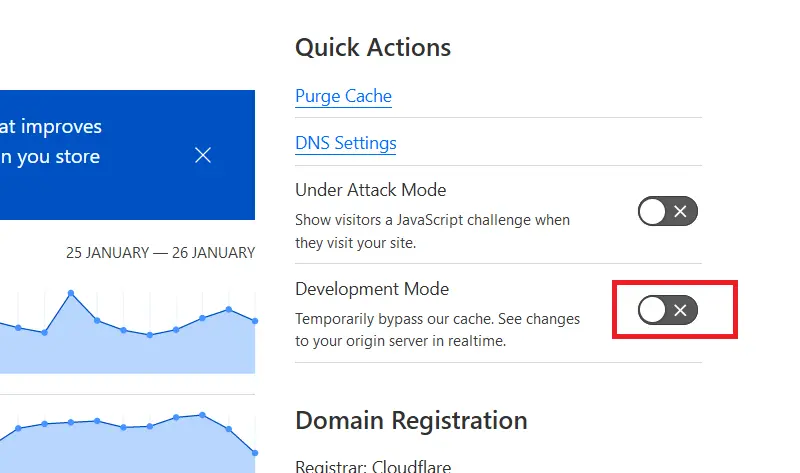
This will make Cloudflare only serve as DNS and nothing else. All caching, security, etc., will be disabled until you enable it again. After pausing it, you must wait for a while as Cloudflare updates and directs all traffic to your origin server. Once that’s done, access your site through another browser like Firefox, and you will now see your original SSL certificate. I recommend using another browser because Chrome takes a long time to update the SSL certificate and will continue showing it for a while.
However, if you wait long enough, even Chrome will eventually update:
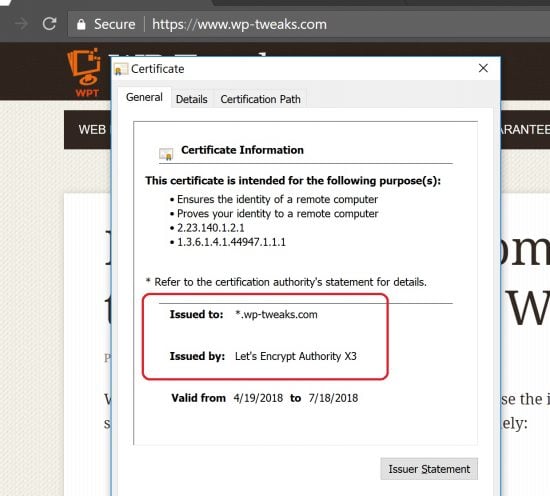
You can see that now it’s showing the correct certificate on the origin server instead of the Cloudflare SSL. Once you’ve verified this, don’t forget to go back to Cloudflare and re-enable it!
So that’s the low down on using an SSL certificate with Cloudflare’s crypto options. It’s certainly possible, and remember that your actual certificate will be hidden unless you pause Cloudflare!
Consider Generating a Cloudflare Origin Certificate
Instead of using Let’s Encrypt, I suggest installing a Cloudflare origin certificate. Let’s Encrypt validation can fail since your traffic passes through a Cloudflare proxy. Moreover, Let’s Encrypt certificates expire once every 90 days, whereas you can generate a Cloudflare certificate for 15 years, so you don’t have to worry about it expiring.
So if you’re fully integrated with Cloudflare, I suggest you eliminate Let’s Encrypt SSL certificates.

I’m having trouble using Cloudflare SSL in conjuction with my Let’s Encrypt ssl certs. It seems I can only use the Let’s encrypt certs if I disable routing through Cloudflare’s systems. How do I set it up to use Cloudflare certs? I bought the domain on namecheap and am using Cloudflare DNS nameservers. My server is running Unraid and I’m using the NginxProxyManager docker. Any help would be greatly appreiciated. Thank you!
I suggest you use Cloudflare’s origin certificates instead of Let’s Encrypt, due to this exact problem. Here’s my tutorial on installing Cloudflare origin SSL certificates: https://www.wp-tweaks.com/how-to-fix-cpanel-autossl-errors-cloudflare-proxy/